
Whitepaper: Understanding the Role of Stolen Credentials in Data Breaches
Defending against cyberattacks is tough, especially when attackers pose as authenticated users on your network. In this whitepaper, we provide the insight you need to understand and stop credential phishing and the subsequent abuse of credentials.
Preventing Credential-Based Attacks
The theft and use of stolen passwords is one of the oldest attacks in the book, yet it remains highly effective. With stolen credentials, an adversary can bypass the entire attack lifecycle by impersonating a valid user, move uninterrupted throughout the organization's network, and shift to the abuse of credentials from within.
PAN-OS® 8.0 neutralizes credential theft by providing prevention capabilities across the attack lifecycle to stop the theft and subsequent abuse of stolen credentials.
The platform identifies and prevents attempts to steal credentials by stopping the submission of valid corporate credentials to illegitimate websites, and neutralizes an attacker’s ability to use stolen credentials for lateral movement and network compromise by enforcing authentication policies at the network layer.
PAN-OS 8.0 introduces new capabilities to neutralize credential theft by adding preventive capabilities to stop the theft and the abuse of passwords across this specific attack lifecycle.
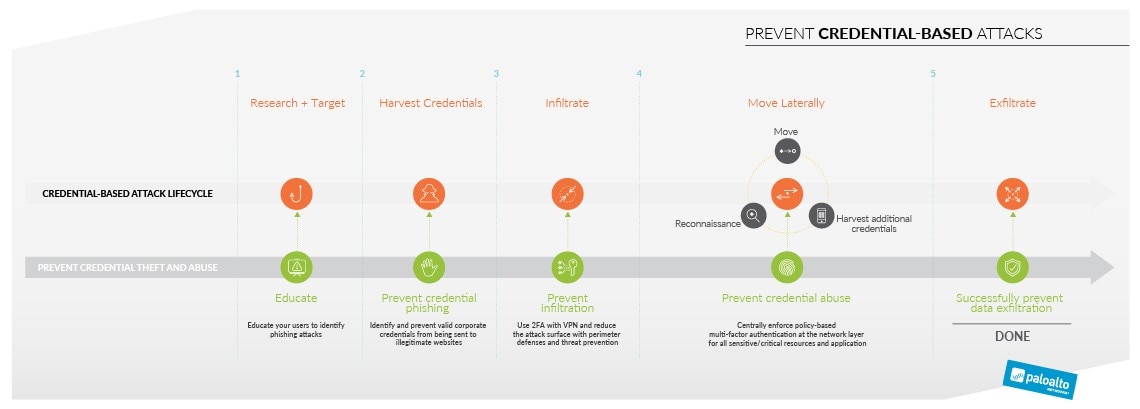
- Stop users from submitting password-based corporate credentials to unknown sites
- Block access to known phishing sites with PAN-DB URL Filtering, using the latest global threat intelligence updated every five minutes
- Protect critical applications and stop attackers from using stolen credentials to conduct lateral movement with policy-based multi-factor authentication enforced at the network level
Demo: Preventing Credential-Based Attacks
Watch our product managers and threat researchers demonstrate how protections in the Palo Alto Networks platform neutralize an attacker's ability to steal credentials, as well as stop them from abusing stolen credentials to gain unauthorized access.
Webinar: Disrupting credential-based attacks
Watch this webinar to learn what you can do today to stop credential theft and abuse. In this session, we will present the specific attack lifecycle for credential-based attacks and demonstrate how you can prevent a successful attack using innovative capabilities delivered by the Palo Alto Networks platform.
Credential Theft: Exposing the Ecosystem and Motives Behind Credential Phishing, Theft and Abuse
In this report, Unit 42® details the ecosystem behind how adversaries steal and leverage legitimate credentials to break-in and move laterally within the organization, often bypassing security controls. Learn the key attack methods currently in use, how this technique fits into attacker playbooks, and real-world guidance on preventing successful attacks.
Live Community
Questions about PAN-OS 8.0? Get quick answers from expert Palo Alto Networks users in the Live Community!
Live Community Discussion Articles



